AI & GitOps Driven Pull Request Reviews with Kubechecks and ArgoCD

Managing Kubernetes deployments at scale requires consistent and secure changes. Kubechecks, integrated with ArgoCD and OpenAI, provides automated, AI-driven reviews that transform this process. Here's how to implement it effectively.
Key Benefits
- Proactive Issue Detection: Analyzes changes before they reach your cluster
- ArgoCD Integration: Provides accurate previews of deployment impacts
- AI-Powered Reviews: Catches both evident and subtle issues in Kubernetes manifests
- Time Efficiency: Reduces manual review time
Real-World Example: Kubechecks in Action
Here's an actual Kubechecks review output that demonstrates its capabilities:
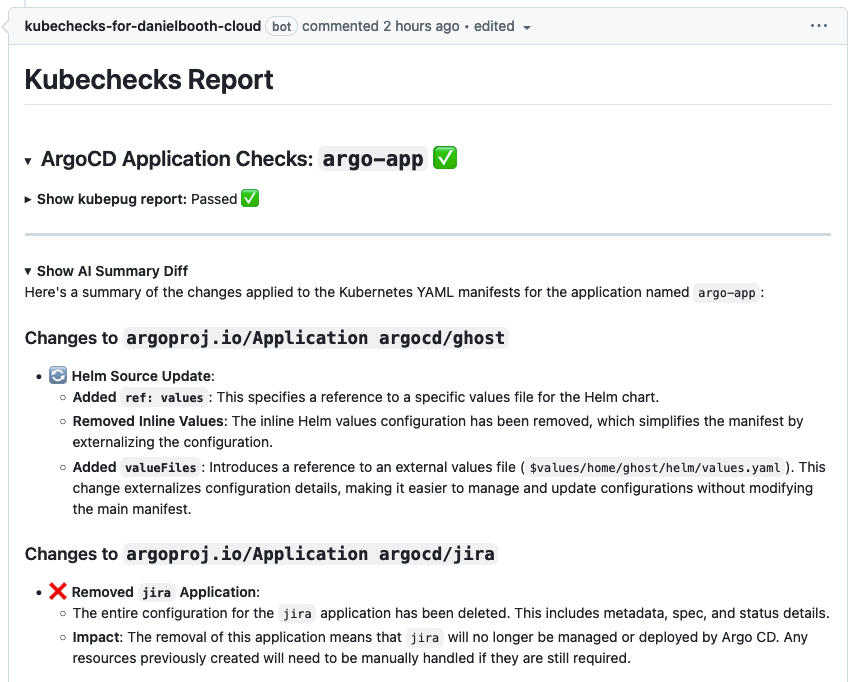
This example shows how Kubechecks provides three key insights:
- Automated validation checks (ArgoCD and Kubepug)
- AI-powered analysis of changes (Comparison to live state in the cluster)
- Clear impact assessment of modifications
For instance, in a recent review, Kubechecks identified:
- Technical changes: Helm value externalization
- Operational impacts: Jira application removal process
- Configuration validations: Resource constraints and dependencies
This highlights how Kubechecks strengthens DevOps workflows by automating validation, providing AI-driven analysis, and clearly communicating deployment impacts. In our example, it caught both technical changes (like Helm value externalization) and operational effects (like the Jira application removal), demonstrating its value in maintaining deployment safety at scale.
Let's ensure the necessary components are in place to implement these capabilities and start benefiting from automated reviews ourselves.
Prerequisites
Before we begin, ensure you have:
- A running Kubernetes cluster
- ArgoCD installed and configured
- GitHub/GitLab repository access
- OpenAI API access
1. Initial Kubechecks Setup
First, let's deploy Kubechecks using a helmfile:
Repositories:
- name: kubechecks
url: https://zapier.github.io/kubechecks/
releases:
- name: kubechecks
namespace: kubechecks
chart: kubechecks/kubechecks
version: 0.5.32. Configure ArgoCD Integration
Connect Kubechecks to your ArgoCD installation:
configMap:
env:
KUBECHECKS_ARGOCD_WEBHOOK_URL: http://argocd-server.argocd.svc.cluster.local/api/webhook
KUBECHECKS_ARGOCD_API_SERVER_ADDR: "argocd-server.argocd.svc.cluster.local"
KUBECHECKS_ARGOCD_API_INSECURE: "true"
KUBECHECKS_ARGOCD_REPOSITORY_ENDPOINT: "argocd-repo-server.argocd.svc.cluster.local:8081"3. Enable OpenAI Integration
Set up AI-powered reviews by configuring the OpenAI integration:
configMap:
env:
KUBECHECKS_OPENAI_API_TOKEN: "your-api-token"4. Configure GitHub/GitLab Integration
We explored two authentication approaches for GitHub integration:
GitHub App Authentication:
configMap:
env:
KUBECHECKS_VCS_TYPE: "github"
KUBECHECKS_GITHUB_APP_ID: "<app-id>"
KUBECHECKS_GITHUB_INSTALLATION_ID: "<installation-id>"
KUBECHECKS_GITHUB_PRIVATE_KEY: "<private-key>"Personal Access Token (PAT):
configMap:
env:
KUBECHECKS_VCS_TYPE: "github"
KUBECHECKS_VCS_TOKEN: "<pat-token>"We found that while GitHub Apps provide finer-grained permissions and better security, PAT authentication can be simpler to set up and debug initially.
5. Set Up Ingress Configuration
Configure webhook access:
ingress:
create: true
className: "cloudflared"
annotations:
cert-manager.io/issuer: cloudflare-origin-issuer
hosts:
kubechecks.yourdomain.com:
paths:
- path: "/hooks/github/project"
pathType: ExactTroubleshooting Common Issues
- Connection IssuesVerify ArgoCD endpointsCheck network policiesValidate webhook configurations
- Review ProblemsMonitor OpenAI API limitsCheck log levels for debuggingVerify webhook payloads
Conclusion
Implementing Kubechecks with ArgoCD and AI-driven reviews can significantly improve your Kubernetes deployment workflow. By following this guide, you've set up an automated system that helps catch issues early and maintains high standards in your deployments.